A new banking malware for Android, dubbed Crocodilus, forces users to provide seed phrases for cryptocurrency wallets, allegedly to create a backup copy. The banker also has the ability to intercept control over the device, collect data and remotely control it.
According to ThreatFabric experts , the malware is distributed using its own dropper, which bypasses the protection of Android 13 (and newer versions). The dropper installs malware without triggering Play Protect, and also bypasses restrictions on access to the Accessibility Service.
Once launched, Crocodilus gains access to the Accessibility Service, allowing it to view screen contents, perform navigation gestures, and monitor app launches.
When a victim opens a targeted banking or cryptocurrency app, Crocodilus loads a fake overlay on top of the real app to intercept credentials.
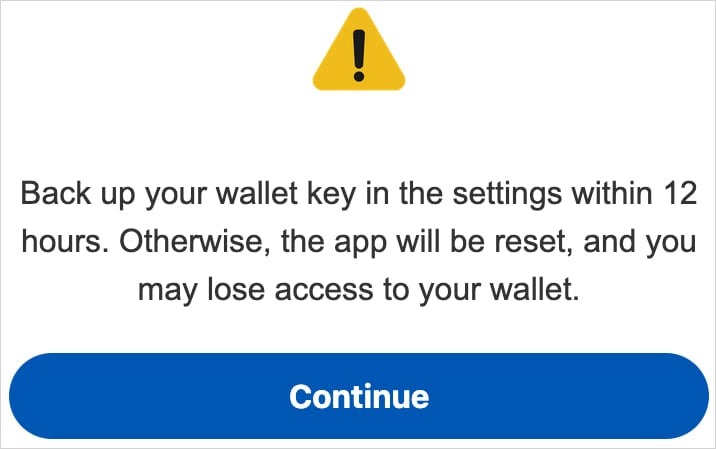
Crocodilus uses social engineering to trick victims into revealing their crypto wallet seed phrases. It does this by using a special overlay that warns users that they supposedly need to “save the wallet key in the settings within 12 hours” or they may lose access forever.
“This trick tricks the victim into logging in to their seed phrase (wallet key), which allows Crocodilus to intercept the text using Accessibility Logger,” the researchers explain. “With this information, the attackers can take full control of the wallet and empty it completely.”
Crocodilus mainly targeted users from Turkey and Spain, as well as bank accounts of users from these two countries. According to debug messages, the malware is of Turkish origin.
It is unclear how the initial infection occurs. Typically, such campaigns trick victims into downloading droppers via malicious websites, fraudulent social media or SMS promotions, or third-party app stores.
The malware's bot component supports 23 commands that it can execute on an infected device. Among them:
- enable call forwarding;
- launch a specific application;
- sending push notification;
- sending SMS to all contacts or to a specified number;
- receiving SMS messages;
- request administrator privileges;
- enable black overlay;
- turn sound on/off;
- screen lock;
- Set yourself as the default SMS manager.
Crocodilus also has remote access trojan (RAT) functionality, meaning malware operators can interact with the device's screen, navigate the user interface, swipe, and more.
There is also a special command for taking screenshots in the Google Authenticator app and intercepting one-time codes used to protect accounts with two-factor authentication.
While performing such actions, Crocodilus operators may activate a black overlay or mute the device to hide the activity from the victim and create the impression that the device is locked.
While the Crocodilus campaign is currently limited to Spain and Turkey, researchers warn that the Trojan could expand its attacks and add new applications to its list of targets.