 Experts from the Solar 4RAYS team of the Solar Group of Companies have discovered a new malware called Webrat . It spies on victims via desktop broadcasting or webcam, steals data from browsers, information about crypto wallets, and hijacks Steam, Discord, and Telegram accounts. Webrat is distributed under the guise of cheats for popular games (including Rust, Counter Strike, and Roblox) and popular software.
Experts from the Solar 4RAYS team of the Solar Group of Companies have discovered a new malware called Webrat . It spies on victims via desktop broadcasting or webcam, steals data from browsers, information about crypto wallets, and hijacks Steam, Discord, and Telegram accounts. Webrat is distributed under the guise of cheats for popular games (including Rust, Counter Strike, and Roblox) and popular software.
The first versions of Webrat began appearing in January 2025 and are sold to attackers through a closed channel called Malware-as-a-Service.
It is noted that experts from DeXpose wrote about the old version of this threat, then known as SalatStealer, in March . Now a distribution channel has been discovered where the malware is distributed under the name Webrat, and it is still in the active development stage.
Basically, the malware functions as a stealer, that is, it hijacks Steam, Discord, and Telegram accounts, as well as steals crypto wallet data, and so on.
In addition, Webrat is capable of downloading additional malware (lockers, miners) to the victim's machine, and the personal information it collects can become a tool for blackmail or swatting (falsely calling the police to the victim's address). In addition, the malware has the ability to fully intercept control over the infected machine through the user interface (UI).
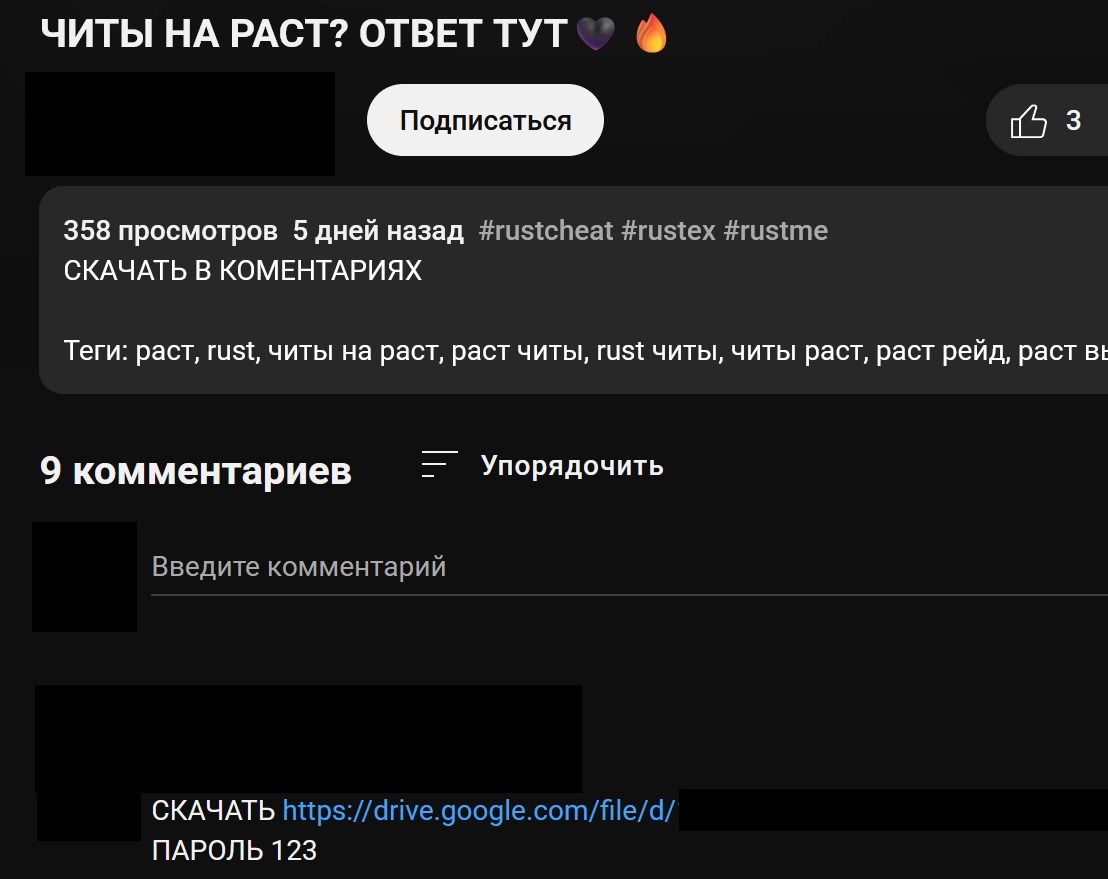
Researchers write that Webrat is most often distributed under the guise of cheats for various games, as well as “fixes” for applications blocked in the Russian Federation (for example, Discord).
Thus, attackers post tutorials on installing programs on YouTube, where they demonstrate the tool's operation and the installation process. As a rule, to install such a "cheat", it is suggested to download a password-protected archive. Information about it is posted in the video description, and the link itself is in the comments.
Other operators distribute Webrat via GitHub under the guise of various utilities. Some of these programs actually have legitimate functionality to lull victims into a false sense of security.
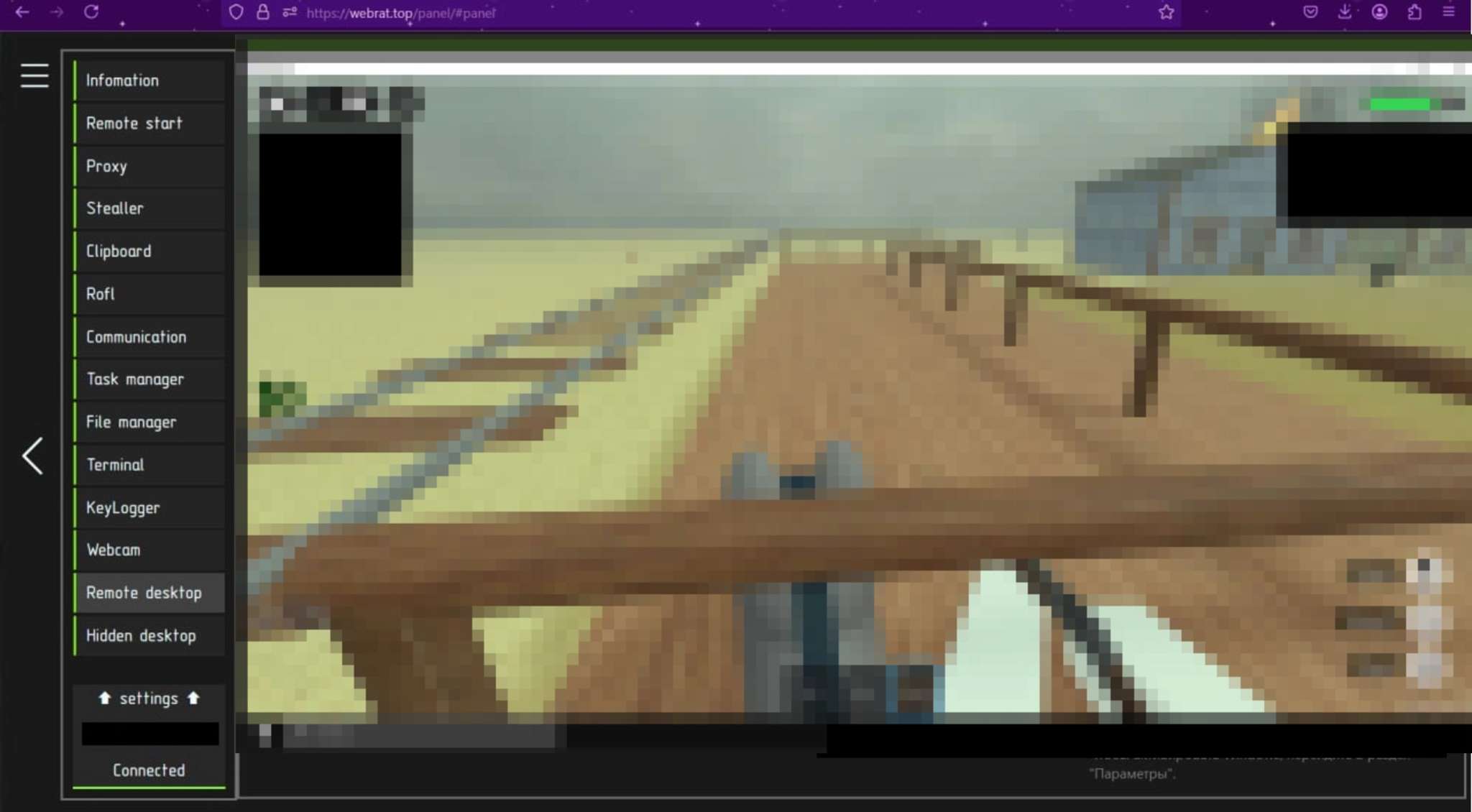
Webrat offers its operators a wide range of tools to manage the infected system. It provides both traditional RAT functionality (terminal, proxy, file exfiltration) and such features as Hidden Desktop, advanced stealer, desktop streaming, webcam capture.
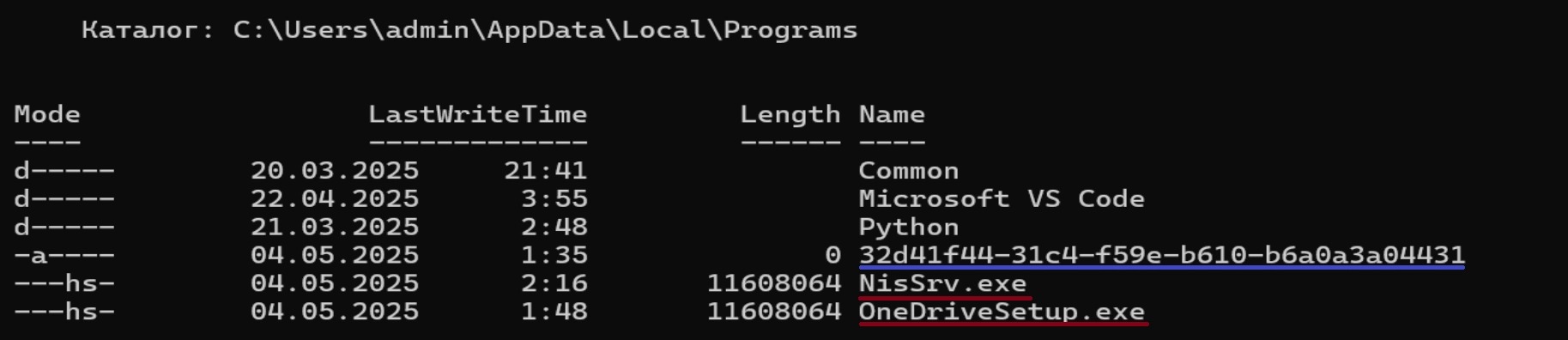
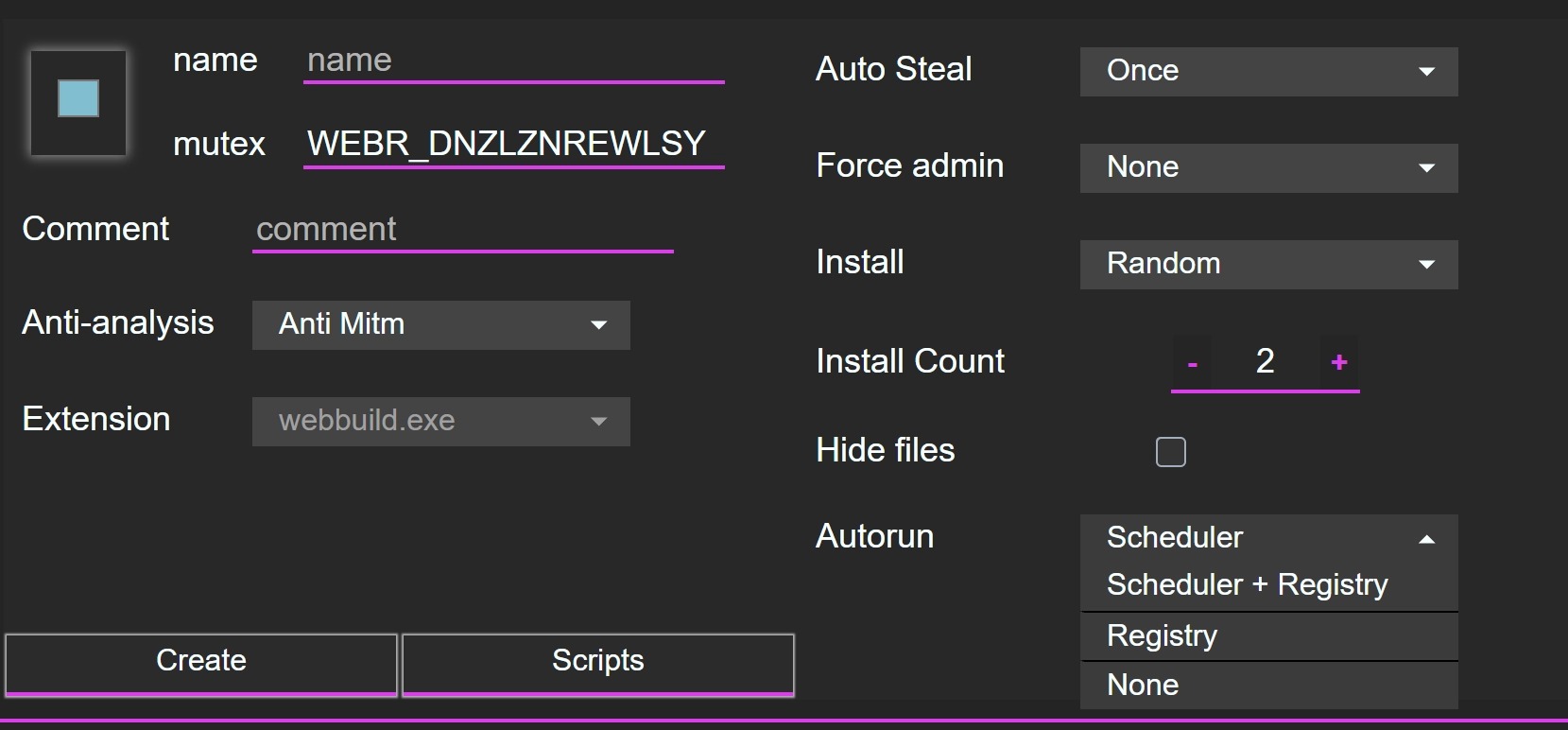
To deploy to the victim's system, Webrat selects a random folder in %localappdata%, %programfiles(x86)% or %programfiles%, as well as the name of a random process running in the system. The malware is fixed in the system via the registry and task scheduler. Several installations can be created at once (according to install count). A file with the victim's ID is created in the installation directory.
The malware writes itself to the registry SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run. This task differs from other malware by its unusual executable file path (NisSrv.exe is located in %localappdata%\Programs instead of C:\Program Files\Windows Defender\). Also, one of the indicators of infection is the hidden mode of the executable file.
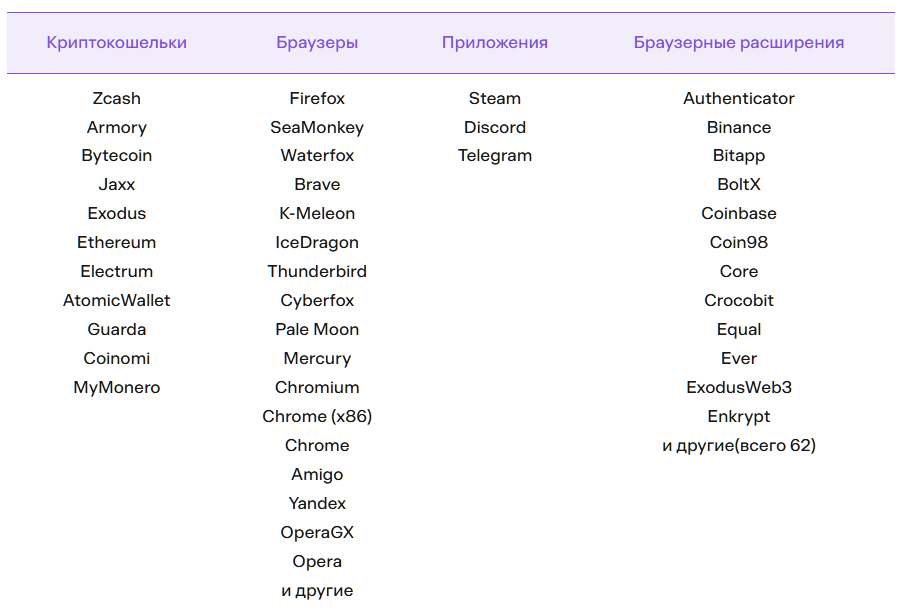
The stealer component supports many different applications. At the beginning, it creates mappings of applications and paths where they store storage files or user sessions. Webrat also has separate functions for stealing Discord, Steam, Telegram session data.
As a result, the attacker receives an archive containing:
• UserInformation.txt — basic information about the PC (HWID, username, PC name, PC characteristics, build information);
• Monitor N.jpg — a screenshot from monitor number N;
• Clients\ directory — contains TXT files with tokens for Discord, Steam, etc.;
• Browsers\Cookies, Browsers\Logins, Browsers\Token directories — contains information about logins, cookies, and tokens;
• Extensions\ directory — information about extensions.
The malware developers also created their own library, salat, to capture the victims' computer screen. Screen capture is launched by creating an additional Webrat process with a single argument, "-". A WebSocket session is used to stream the screen. All this is complemented by the Hidden Desktop function, which allows you to control the victim's screen interactively.
The above-mentioned surveillance via webcam is carried out using the ffmpeg utility, via DirectShow for subsequent processing of the video stream with the specified parameters. Video from the webcam is broadcast in real time to the malware control panel.
Webrat also has a microphone listening function, which allows it to record the victim's conversations on the computer. As with the webcam, listening is carried out using the ffmpeg utility.
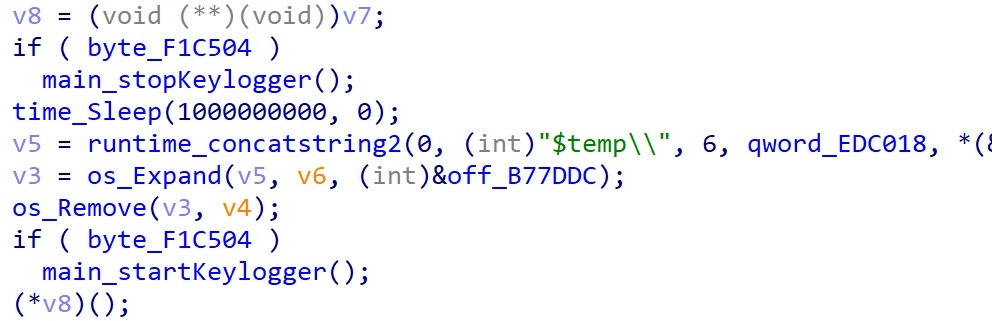
In addition, Webrat has keylogger functionality, which is launched by creating a separate process with the argument "k". The PID of its process is written to a global variable.
The keylogger process runs the main_runKeylogger function, which hooks into keyboard input and monitors and logs the user's active window. All input, including status key presses (ctrl, shift, capslock), is saved to a file in the %TEMP%\
To manage the malware, the developers provide a web server with an expanded control panel. Subscription management for the malware is also carried out here: there is a separate tab for this, where you can enter the activation code. The number of victims is displayed in the upper right corner of the panel.
The web panel also has a builder for assembling malware with various parameters, the interface of which can be seen below.